http://www.tail-f.com.ar/servicios/httpd/nginx/nginx-como-proxy-reverso-en-servidor-directadmin.html adresinde orjinali
ispanyolca . Anlamiyorum. Translate ettirip ingilizcesinden bir anlam cikarmaya calistim. Basarili oldum.
This time I will explain how to install Nginx as a reverse proxy server with DirectAdmin hosting.
What is a reverse proxy?
A reverse proxy in this case is basically a web server that stands as a layer between the client and a backend, so as to optimize the connection. Typically, the proxy server is a lightweight frontend that works, handles requests from HTTP clients and derives a backend processing could be an Apache server. Depending on the configuration that we apply, a proxy allows us to introduce more security in our network, making load balancing, to cache, etc.
It also optimizes the memory management. We think that Apache launches a thread or process for each new customer, which is closed only when data transfer ends. If the client has a slow connection, even though Apache running fast, the process is running until the completion of sending data. A light as Nginx frontend allows the process to wait for the customer is much lighter than an Apache.
Finally, as indicated in sysadmin.es , a proxy Nginx serves to prevent denial of service attacks using slowloris .
A reverse proxy on a server hosting
Proxies are commonly used in architectures to serve high-demand sites. In such cases is common, for example, make Apache serve dynamic content and a lighter server (lighttpd or nginx) serve static content. But in a hosting server that is not so simple, because by staying several sites on the same computer our setup should be as generic as possible in order to serve most of our customers. As we shall see, we can define some kind of cache, but also must be generic enough to not cause problems. We also have to think about integration with control panel we use. I use DirectAdmin, and this panel does not (yet) a native integration with other web server than Apache.
Nginx + Apache + DirectAdmin
The option that I present is to use Nginx as reverse proxy, managing client connections and doing a very basic static content caching. The guide is intended for CentOS, but in other operating systems should not be too different.
First install Nginx. The process is simple.
# cd /usr/src
# wget http://nginx.org/download/nginx-0.8.54.tar.gz
# tar zxvf nginx-0.8.54.tar.gz
# cd nginx-0.8.54
# ./configure --prefix=/usr \
--conf-path=/etc/nginx/nginx.conf \
--error-log-path=/var/log/nginx/error.log \
--http-log-path=/var/log/nginx/access.log \
--pid-path=/var/run/nginx/nginx.pid \
--lock-path=/var/run/nginx/nginx.lock \
--with-http_stub_status_module \
--with-openssl=/usr/lib/openssl
# make && make install
Create the directory to save the cache static content:
# mkdir -p /var/tmp/nginx
# chown apache:apache /var/tmp/nginx
The most important thing is to configure Nginx. To do this modify / etc / nginx / nginx.conf to make it something like this:
Important: __SERVER_IP__ replace the __SERVER_HOSTNAME__ server IP and the name of the server.
user apache;
worker_processes 5;events {
worker_connections 8192;
}http {
server_tokens off;include mime.types;
default_type application/octet-stream;log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';#access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;keepalive_timeout 75 20;
gzip on;
server_names_hash_bucket_size 64;
reset_timedout_connection on;client_max_body_size 100m;
# Main cache data
proxy_cache_path /var/tmp/nginx/cache levels=1:2 keys_zone=staticfilecache:180m max_size=500m;
proxy_temp_path /var/tmp/nginx/proxy;
proxy_connect_timeout 30;
proxy_read_timeout 120;
proxy_send_timeout 120;
proxy_cache_key "$scheme$host$request_uri";server {
listen __SERVER_IP__:81;
server_name __SERVER_HOSTNAME__ _;#charset koi8-r;
charset off;access_log off;
#access_log /var/log/nginx/access.log main;# Main reverse proxy for most requests
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;proxy_pass http://__SERVER_IP__; # apache here
client_max_body_size 16m;
client_body_buffer_size 128k;#proxy_buffering off;
proxy_buffering on;proxy_connect_timeout 90;
proxy_send_timeout 90;
proxy_read_timeout 120;
proxy_buffer_size 8k;
proxy_buffers 32 32k;
proxy_busy_buffers_size 64k;
proxy_temp_file_write_size 64k;error_page 502 503 /50x.html;
}# Proxy cache for static files
location ~* \.(jpg|png|gif|jpeg|css|js|mp3|wav|swf|mov|doc|pdf|xls|ppt|docx|pptx|xlsx)$ {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;proxy_pass http://__SERVER_IP__; # apache here
client_max_body_size 16m;
client_body_buffer_size 128k;#proxy_buffering off;
proxy_buffering on;proxy_connect_timeout 90;
proxy_send_timeout 90;
proxy_read_timeout 120;
proxy_buffer_size 8k;
proxy_buffers 32 32k;
proxy_busy_buffers_size 64k;
proxy_temp_file_write_size 64k;# Proxy cache data
proxy_cache_valid 200 120m;
expires 864000;
proxy_cache staticfilecache;error_page 502 503 /50x.html;
}#error_page 404 /404.html;
# redirect server error pages to the static page /50x.html
#
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root /var/www/html;
}}
}
Of course this is a basic configuration that should be adapted to the specific case. It is important to note the following:
Nginx listens on port 81 and Apache in 80. This is important to avoid having to make changes in the configuration of DirectAdmin.
3 Locations are defined. The first two are proxies that happen are thinking of Requests to Apache on port 80. The second applies only to the Requests for static files and do a cache in / var / tmp / nginx. This cache is managed by following the appropriate HTTP headers.
Now we need to install an Apache module, mod_rpaf, to use the header X-Real-IP.
# cd /usr/src
# wget http://stderr.net/apache/rpaf/download/mod_rpaf-0.6.tar.gz
# tar zxvf mod_rpaf-0.6.tar.gz
# cd mod_rpaf-0.6
# apxs -i -c -n mod_rpaf-2.0.so mod_rpaf-2.0.c
And then add this to httpd.conf
LoadModule rpaf_module /usr/lib/apache/mod_rpaf-2.0.so
RPAFenable On
RPAFsethostname On
RPAFproxy_ips 127.0.0.1 __SERVER_IP__
RPAFheader X-Forwarded-For
__SERVER_IP__ Replacing the server’s IP.
We will also need an init script for nginx. As I found a fact, I did this:
nano /etc/init.d/nginx
#!/bin/bash
#
# Name: NginX, tsj5j
#
# Function: Start up NginX
#
# chkconfig: - 85 15
# description: NginX starter# Source function library.
. /etc/rc.d/init.d/functions# Source networking configuration.
. /etc/sysconfig/networkprog="nginx"
nginx=/usr/sbin/nginxstart () {
echo -n $"Starting $prog: "
$nginx
RETVAL=$?
return $RETVAL
}stop () {
echo -n $"Stopping $prog: "
killproc $nginx
RETVAL=$?
return $RETVAL
}reload () {
echo -n $"Reloading $prog: "
killproc $nginx -HUP
RETVAL=$?
return $RETVAL
}case "$1" in
start)
start
;;
stop)
stop
;;
restart)
stop
sleep 1
start
;;
reload)
reload
;;
graceful)
reload
;;
esacexit $RETVAL;
Once you locate that content in a file / etc / init.d / nginx enabled him
# chmod +x /etc/init.d/nginx
# chkconfig --add nginx
# chkconfig nginx on
# service nginx start
And we lack one thing. We have Apache running on port 80, and nginx in 81. How do we make Nginx serving the requests of our customers? Create a route on iptables to redirect port 81 traffic to 80:
# iptables -t nat -A PREROUTING -p tcp -s ! __SERVER_IP__ --dport 80 -j REDIRECT --to-ports 81
# service iptables save
__SERVER_IP__ Replacing the server’s IP.
And presto, now our Nginx will receive all HTTP traffic and negotiate with the Apache to return to customers.
Verify that meets Nginx
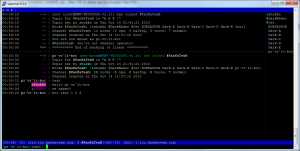
Check that Nginx is handling the requests on port 80 is very easy to do with curl. For example, testing it against the URL of this blog.
curl -I blablabla.com
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 15 Dec 2010 04:54:35 GMT
Content-Type: text/html
Connection: keep-alive
Keep-Alive: timeout=20
Last-Modified: Sun, 21 Nov 2010 00:20:20 GMT
ETag: "1de7a9-1c2-495851ad1f900"
Accept-Ranges: bytes
Content-Length: 450
Vary: Accept-Encoding,User-Agent
As we see the Nginx server is serving.
Iste bu kadar
gule gule kullaniniz 🙂