soru:
how to find which ips are in use ?
Hello
I’ve got a 3 host cluster proxmox system running with 12 openvz installations.
Each openvz vm have 3-5 ip addresses each.
I can find them by entering each vm and clicking network tab.
But checking all 12 vm’s take time.
Is there an easy way to manage ips given to each vm?I mean how can I easily list all used ips in my proxmox cluster system and which ip belongs to which vm id ?
CEVAP:
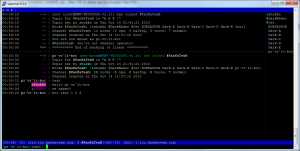
The command I needed is “vzlist”
1 single command:Code:vzlist -o hostname,ctid,ipgives me the exact result I needed.
more info:
http://download.swsoft.com/virtuozzo/virtuozzo4.0/docs/en/win/VzWindowsReference/4549.htm
http://download.swsoft.com/virtuozzo/virtuozzo4.0/docs/en/win/VzWindowsReference/4615.htm